OAuth¶
Introduction¶
OAuth is one of the multiple ways you can authenticate users to 3forge AMI. The 3forge AMI OAuth Plugin makes it easy to integrate AMI with any OAuth based identity manager. It provides a simple standard authentication mechanism and allows you to build access control into your 3forge AMI Layouts.
OAuth Quickstart¶
Quickstart Instructions¶
Prerequisites:
- Find out your identity provider and ensure it allows for OAuth 2.0 Authentication. You will need to know the identity provider url.
- Register a new Web App with your identity provider.
- Provide a Sign In Redirect Url, we recommend
https://<your-server>:33332/oauthRedirectUrl- This will be used in the oauth.redirect.url property
- Provide a Sign Out Redirect Url (Optional but recommended)
- Provide a Sign In Redirect Url, we recommend
How to setup the OAuth Plugin
- Navigate to your 3forge AMI config directory, it's typically located in
ami\amione\config - Create a file called local.properties if one is not already present
- Add the properties from the Minimal Configuration below to the file
local.properties - Update the values of the properties to match your identity provider.
- Restart 3forge AMI
Minimal Configuration¶
Note: Please refer to Properties for a detailed understanding of each property
Properties¶
Required¶
sso.plugin.class=com.f1.ami.web.AmiWebOAuthPluginImplSpecify class to use Oauth SSOoauth.server.domain=https://oauthprovider.comThe domain of the auth server accountweb.logged.out.url=/loggedout.htmSet AMI logged out pageoauth.redirect.uri=http://localhost:33332/oauthRedirectUrl/3forge AMI Url for Oauth server to redirect after loginoauth.client.id=clientidClient IDoauth.client.secret=secretClient secretoauth.authorization.endpoint=/authorizeEndpointAuthorization endpointoauth.token.endpoint=/tokenEndpointToken endpointoauth.scope=openid profile email offline_accessOauth scopeoauth.username.field=emailUser Email
Optional¶
oauth.refresh.token.endpoint=/refreshTokenEndpointThe endpoint to get the refresh tokenoauth.refresh.redirect.uri=/refreshRedirectUriThe refresh redirect uri, by default is null, can be overridenoauth.refresh.scope=/refreshScopeThe refresh scope, by default is null,can be overridenoauth.refresh.client.id=/refreshClientIdThe client Id after refresh, by default is the same as oauth.client.id,can be overridenoauth.refresh.client.secret=/refreshClientSecretThe client Sercret after refresh, by default is the same as oauth.client.secret,can be overridenoauth.ami.isdev.field=emailDev User Emailoauth.ami.isdev.values=List of dev user emailsoauth.access.token.expires.in=expires_inKey that contains the time the access token expires inoauth.code.challenge.method=S256Code challenge methodoauth.digest.algo=SHA-256Java hashing algorithmoauth.session.check.period.seconds=60Seconds to check refresh token expirationami.web.index.html.file=index2.htmThe 3forge AMI endpoint that triggers the build auth request.oauth.debug=trueEnables Debugging Modeoauth.validate.certs=falseDisables certificate validation for SSLoauth.dynamic.redirect=trueEnables access to AMI via both IP address and domain url. (Requires both urls to be registered in your OAuth provider's setting)
Custom OAuth Plugin¶
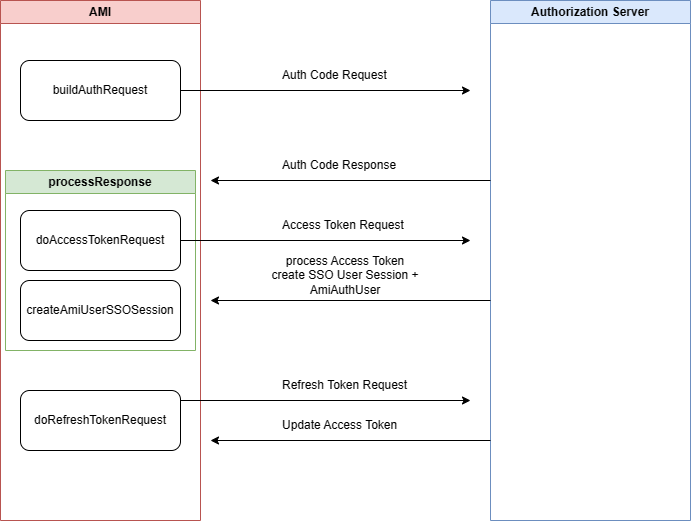
The AMI OAuth plugin handles authorization code and access token requests that are needed for Authenticating to AMI. By extending the 3forge AMI OAuth plugin, you can create your own Ami OAuth Plugin if you have custom requirements for access control or entitlements.
There are three main components to the 3forge AMI OAuth Plugin: buildAuthRequest, processResponse, and createAmiUserSSOSession.
Main Components¶
The <strong>buildAuthRequest </strong>method is responsible for creating the url for the Authorization Code request.
The <strong>processResponse </strong>method is responsible for processing the response from the Authorization Code request, then building an Access Token request. Once it obtains an access token, it needs to return an AmiAuthUser.
The <strong>createAmiUserSSOSession </strong>is responsible for creating the AmiAuthUser and OAuthSSO Session. The AmiAuthUser can be used to set user session variables or restrict access to layouts. The OAuth Session is accessible in AMIScript by session.getSsoSession().
Protocol Diagram¶
Example Java Code¶
Example Configuration¶
OAuth for Okta¶
The Okta plugin is a specific version of the OAuth Plugin, see below for the list of properties requrieD:
sso.plugin.class: The class the implements the AmiWebSSOPlugin. Use com.f1.amioktaauth.AmiOktaOauthPluginoauth.client.id: Client Id of the application registered to authenticate via OKTA.oauth.client.secret: Client secret of the application registered to authenticate via OKTA.oauth.redirect.uri: The uri OKTA will use to redirect the user once authentication is complete. In this case it will be the uri of amiweb (http://localhost:33332/oktaAuthFinished/). Note that this uri must match with the one configured in OKTA account.oauth.server.domain: The domain of the okta account (<https://something.okta.com>)oauth.scope: Space delimited scopes indicating the types of resources AMI will be requesting from the resource server. Use openid profile emailweb.logged.out.url: url to redirect to when logged out, default is / which directs to login page. (Hint: set to /loggedout.htm for a logged out page instead, useful for OAUTH)oauth.authorization.endpoint: Okta authorization endpoint. Default value /oauth2/default/v1/authorizeoauth.token.endpoint: Okta token endpoint. Default value /oauth2/default/v1/tokenoauth.code.challenge.method: Okta code challenge method. Default value S256oauth.oauth.digest.algo: Java hashing algorithm used to verify the code challenge. Default value SHA-256oauth.username.field: The field from Okta identity response to use as the AMI username. Default value emailoauth.ami.isadmin.field: The field from Okta identity response use to identity an AMI admin user (Recommended).oauth.ami.isadmin.values: Comma delimited list of AMI admins. If the value of the isadmin field matches any of the values, the user gets AMI admin privileges. Otherwise the user will be in user mode.oauth.ami.isdev.field: The field from Okta identity response use to identity an AMI dev user (Recommended).oauth.ami.isdev.values: Comma delimited list of AMI devs. If the value of the isdev field matches any of the values, the user gets AMI dev privileges.oauth.debug: For detailed logging. Default value falseoauth.session.check.period.seconds: Controls polling frequency for a refresh token and also the frequency of the reaper thread to check on the SSO session. Defaults to 60 seconds.